📝 Note: This article was last updated on Jan. 21, 2026. We regularly update the information to ensure you have the latest insights! 😊
Introduction
In the design of no-code and low-code platforms, RBAC (Role-Based Access Control) is an unavoidable topic. Whether for team collaboration, data security, or managing multi-module systems, the moment user-resource boundaries appear, roles and permissions become essential.
Developers and enterprise users have long paid close attention to RBAC — it’s not only a pillar of platform security but also a key factor influencing scalability and maintainability.
💬 Hey, you’re reading the NocoBase blog. NocoBase is the most extensible AI-powered no-code/low-code development platform for building enterprise applications, internal tools, and all kinds of systems. It’s fully self-hosted, plugin-based, and developer-friendly. → Explore NocoBase on GitHub
On Reddit, discussions around this topic are constant.
“Every time I try to add user authentication with roles and permissions, things fall apart. The logic seems straightforward, but the execution breaks down, especially once I start layering role-based access.”
He only wanted to set up three roles in a small directory app — regular user, merchant, and admin.
The logic was simple and common, but once implemented, nested permission logic caused system complexity to skyrocket. RBAC quickly became the most error-prone part of the project.
Another kind of confusion often comes from the opposite direction. In the r/nocode community, someone pointed out:
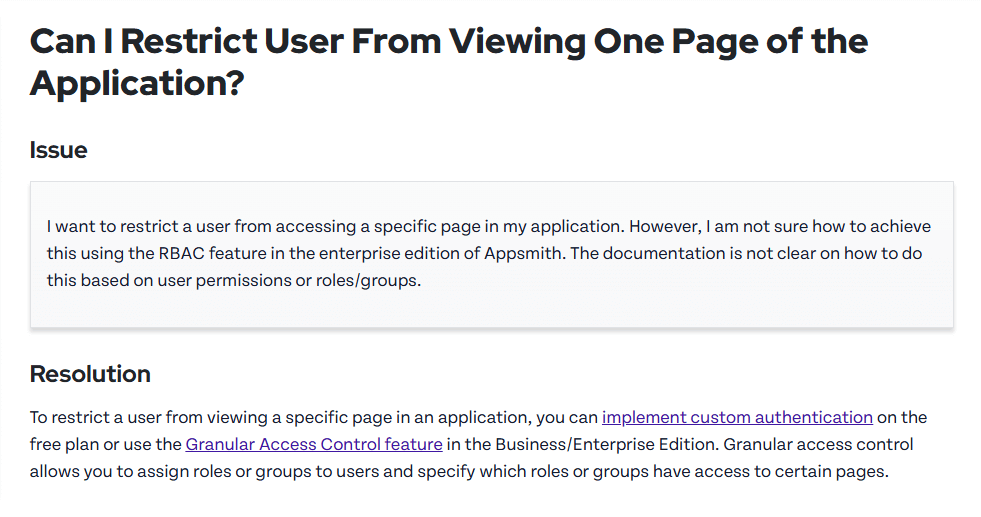
“Budibase says it’s open source, but user limits apply. Appsmith says granular access control is only available in the paid plan.”
Most no-code or low-code platforms still fall short in permission management: either permissions are too coarse, limited to page or module level, or fine-grained role and data access controls are only available in enterprise or paid tiers. As a result, teams are forced to balance security against cost.
At its core, the RBAC model answers a simple question:
Who (User) can perform what (Permission) on which resource (Resource)?
The difficulty lies in the complexity of this mapping within no/low-code environments. Platforms must handle diverse roles — developers, business users, external clients — while managing multiple resource layers such as tables, fields, pages, and workflow nodes. They need to allow visual configuration while ensuring logical consistency — a key challenge many platforms face in implementing RBAC.
In our earlier article, “How to Design an RBAC (Role-Based Access Control) System” we explored this mechanism in depth — from how roles and resources are abstracted, to designing field- and condition-level permissions, and maintaining clear boundaries in multi-role collaboration. Those insights provide the foundation for this article — understanding how various platforms balance trade-offs in RBAC implementation.
In this comparison, we evaluate six representative no/low-code platforms — NocoBase, Retool, OutSystems, Appsmith, Budibase, and Mendix — across three dimensions: permission granularity, flexibility, and user experience.
Before we dive into each platform, here’s an overview table highlighting their main differences and characteristics 👇
For reference:
★ = Coarse granularity
★★★★★ = Fine granularity
| Platform | Open Source | Permission Granularity | Flexibility | User Experience |
|---|---|---|---|---|
| NocoBase | Open source (self-hosted) | ★★★★★ Field-, condition-, action-, and API-level permissions with visual rule configuration. | High — plugin-based architecture with an extensible permission model. | Intuitive visual setup, ideal for multi-role teams. |
| Appsmith | Open source (community edition) | ★★★★☆ Page-, query-, and data source-level permissions; some advanced features are paid. | High — supports both preset and custom roles, with attribute-level access control. | User-friendly interface and low learning curve. |
| Budibase | Open source (self-hosted) | ★★★★ Table-, view-, and page-level permissions; limited conditional logic. | Medium-high — supports role hierarchy and conditional rules. | Easy to configure, great for small to mid-sized teams. |
| Mendix | Proprietary / Commercial | ★★★★ Module-, entity-, page-, and process-level permissions. | Medium — flexible but requires developer participation. | Stable and enterprise-oriented with strong governance. |
| Retool | Proprietary / Commercial | ★★★★ App/resource/query-level permissions; enterprise edition adds row-level security. | Medium-high — uses permission groups and resource rules. | Powerful but complex to configure and relatively costly. |
| OutSystems | Proprietary / Commercial | ★★★★ Screen-, module-, and data-level permissions; custom extensions required. | Medium — clear structure but limited flexibility. | Enterprise-grade security with a mature model. |
NocoBase
🔗 Official Site: https://www.nocobase.com
📘 Documentation: https://docs.nocobase.com/handbook/ui/actions/permission
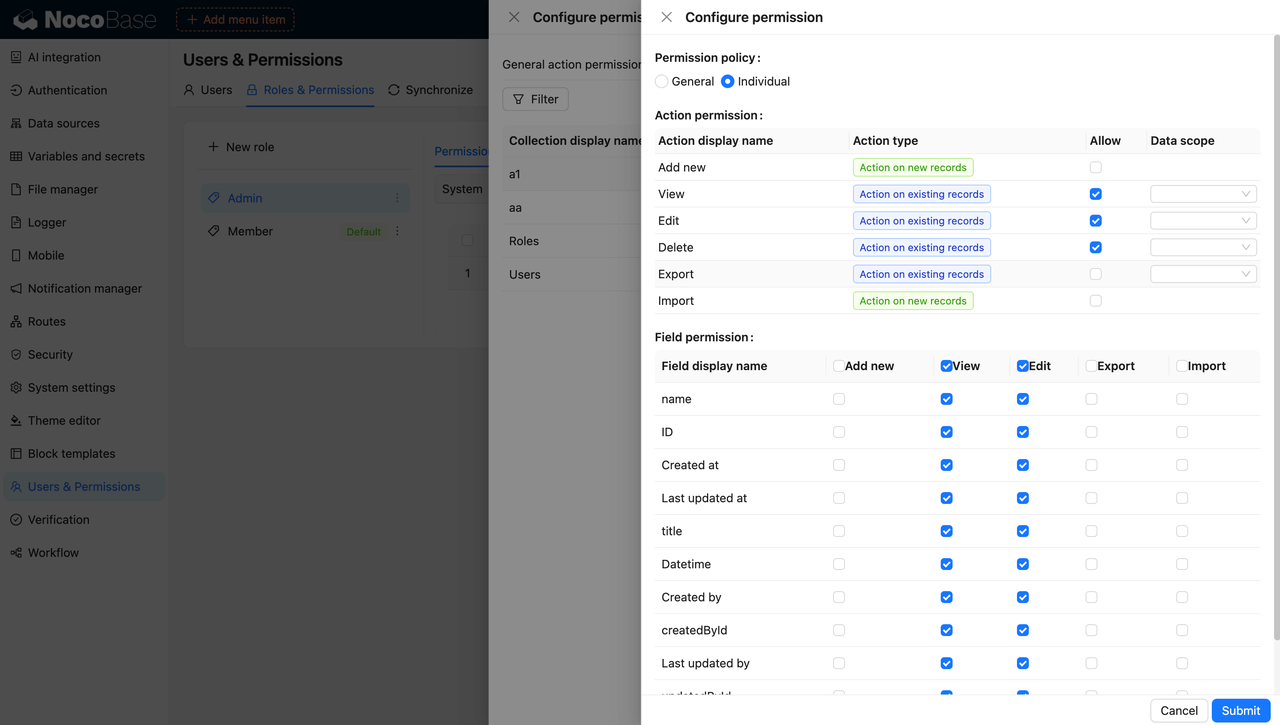
- Permission Granularity: ★★★★★ Covers field, condition, view, action, and API levels.
- Features: Enables multi-layer, role-based access management with flexible resource-level rules. Supports both field and condition filters, and allows permissions to be linked to specific views or actions.
- User Experience: Offers a WYSIWYG-style interface where permissions can be visually configured, lowering the barrier for setup. Non-technical users — such as product managers and operations teams — can handle most standard configurations.
- Extensibility: Built on a plugin-based framework, supporting external authentication (OAuth, SSO, LDAP), custom logic extensions, and advanced identity integrations. Enterprises can define complex access policies or connect unified login systems.
- User Feedback: Users in official NocoBase videos highlighted its powerful RBAC features and overall cost efficiency.

Appsmith
🔗 Official Site: https://www.appsmith.com
📘 Documentation: https://docs.appsmith.com/advanced-concepts/granular-access-control
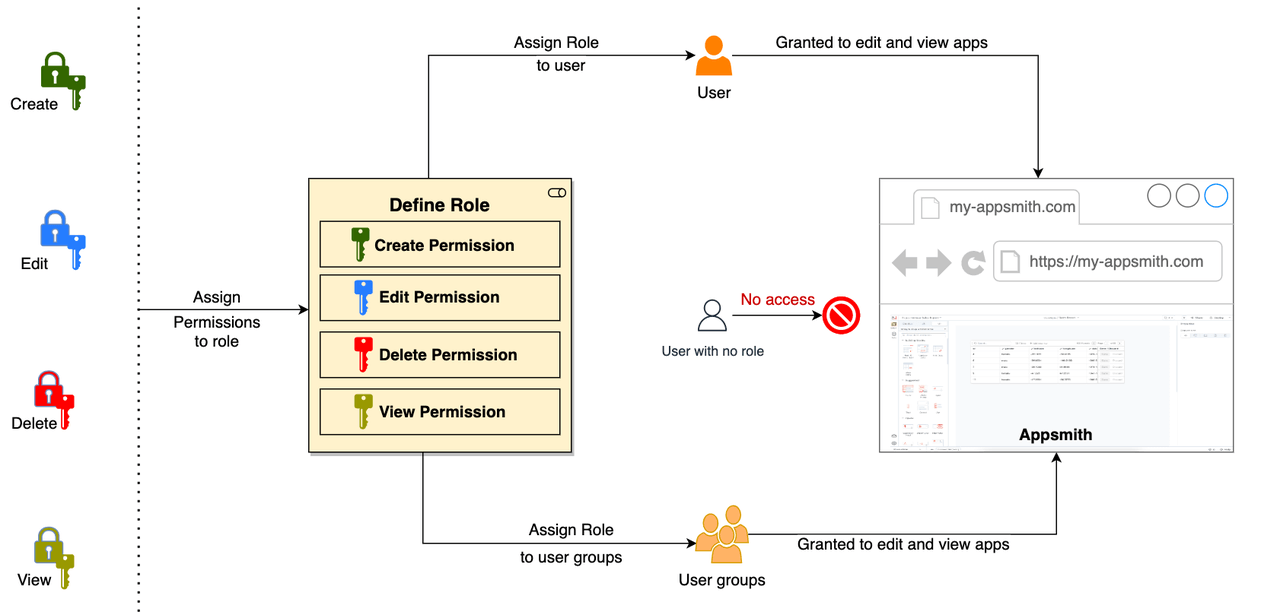
- Permission Granularity: ★★★★☆ Covers app, page, query, and data source levels; enterprise users can define attribute-level access.
- Features: Provides a built-in Granular Access Control system with role inheritance and customizable permission fields. Supports collaborative editing and workflow-linked access control.
- User Experience: Clean, intuitive interface for managing users, teams, and resources in one place. Syncs permissions across development, staging, and production environments to enhance collaboration.
- Extensibility: Integrates with OAuth, SAML, and OpenID; supports external access control through REST APIs.
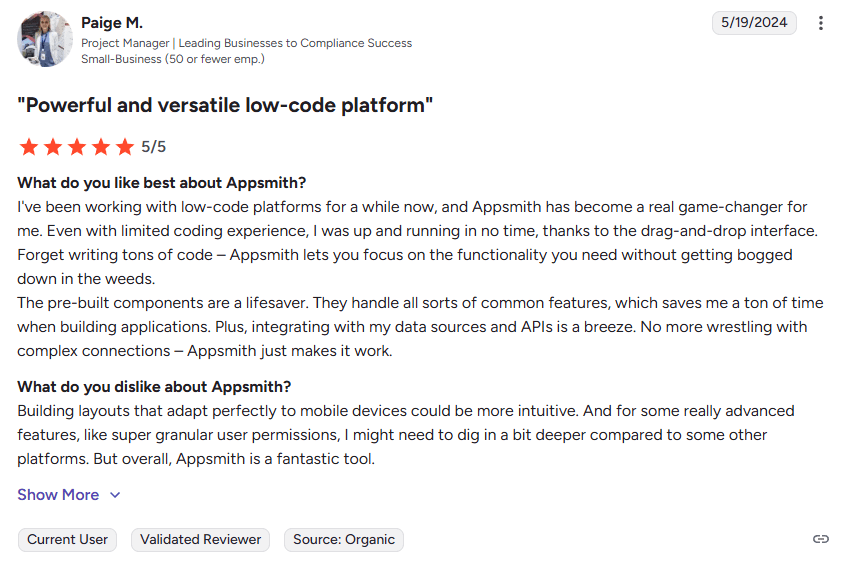
- User Feedback: Some community members note the free version lacks fine-grained control, with advanced features available only in the enterprise plan.
Budibase
🔗 Official Site: https://www.budibase.com
📘 Documentation: https://docs.budibase.com/changelog/rbac
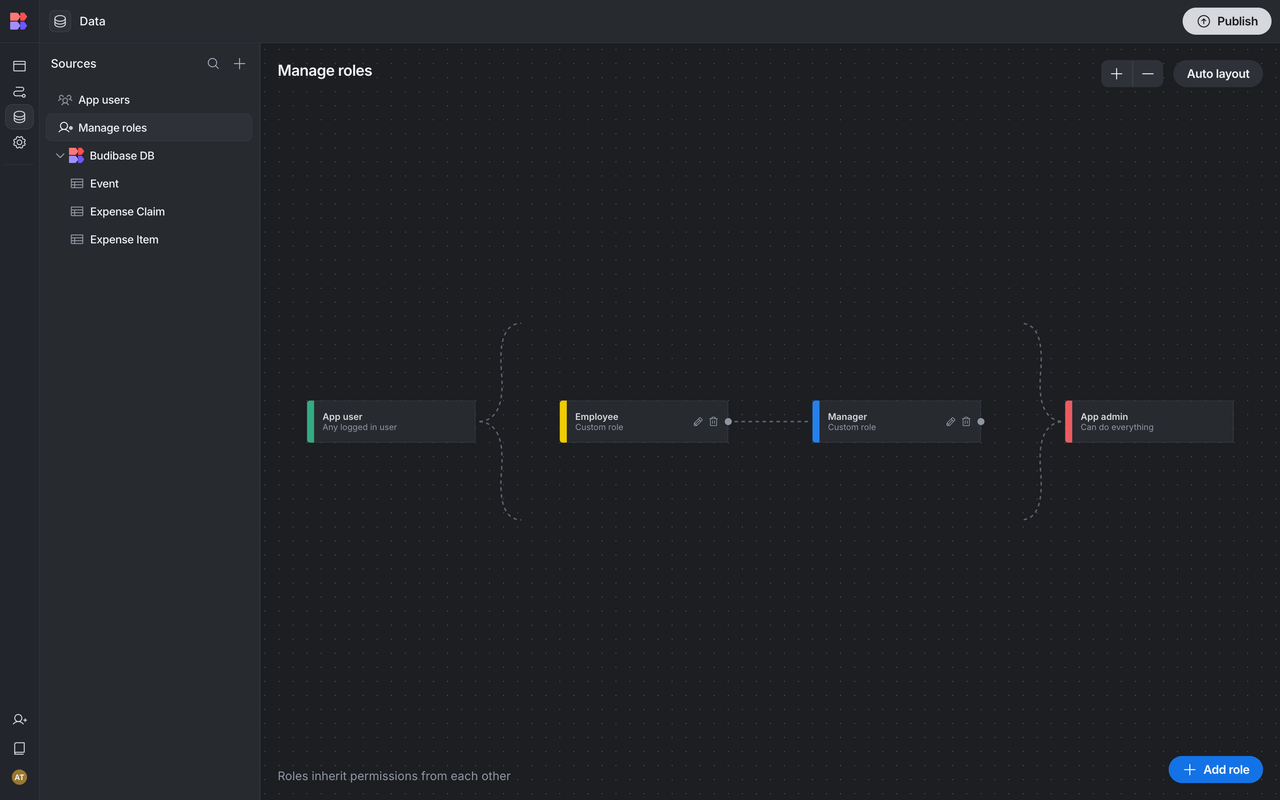
- Permission Granularity: ★★★★ Table-, view-, and page-level control; custom logic needed for field and condition-level permissions.
- Features: Includes a native Role-Based Access Control module for managing visibility, access rights, and actions across roles. Supports dynamic data filtering and multi-role combination strategies.
- User Experience: Visual interface with drag-and-drop role mapping and easy setup — ideal for small and medium teams without full-time developers.
- Extensibility: Provides REST API and Webhook support for connecting third-party authentication or internal gateways, plus automated role syncing.
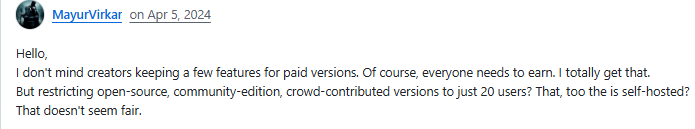
- User Feedback: Community users appreciate its “complete and open-source” design, especially the RBAC module and self-hosting flexibility. However, the self-hosted free version limits accounts to 20 users, leading to debate over its “fully open” claim.
Mendix
🔗 Official Site: https://www.mendix.com
📘 Documentation: https://docs.mendix.com/refguide9/user-roles/
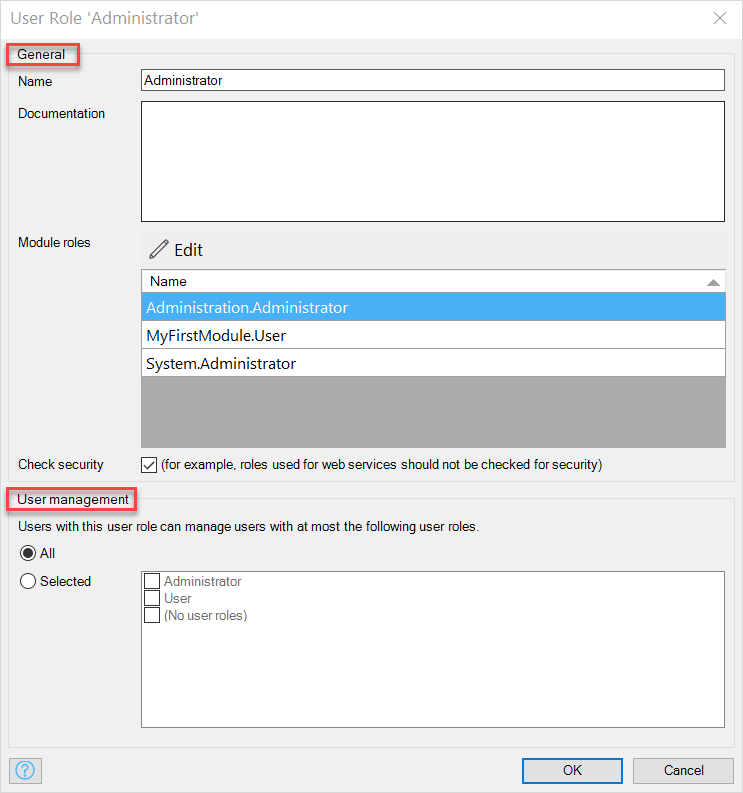
- Permission Granularity: ★★★★ Controls access at the module, entity, page, and microflow levels.
- Features: Uses a dual-layer mapping model (Module Roles → User Roles) to define fine-grained access, including specific page elements, buttons, and data sources.
- User Experience: Enterprise-grade security and a clear interface, though setup can be lengthy. Cross-team projects require extra governance and synchronization.
- Extensibility: Allows extending logic through Java actions or microflows, with integrations for identity systems like Azure AD and Okta.
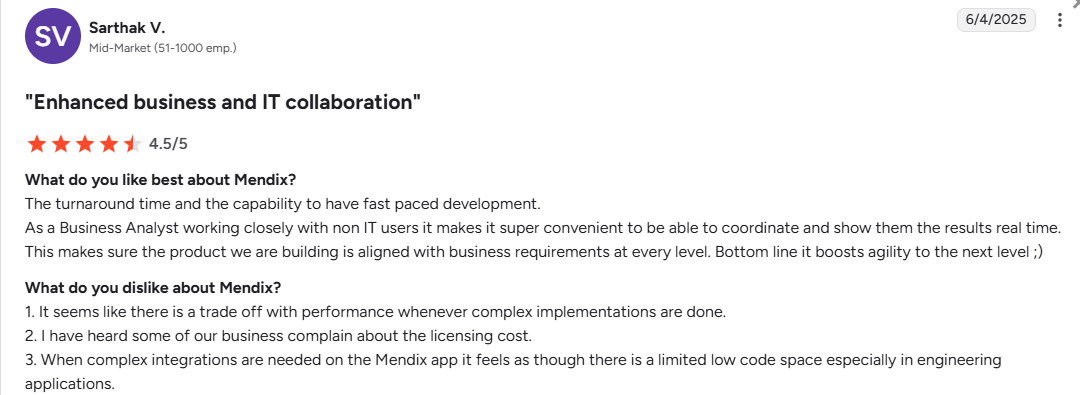
- User Feedback: Developers on G2 praised its solid permission model and fast adaptation to business needs but noted that complex implementations reduce performance and increase licensing costs. The low-code layer can also feel restrictive in large integrations.
Retool
🔗 Official Site: https://retool.com
📘 Documentation: https://docs.retool.com/permissions/quickstart
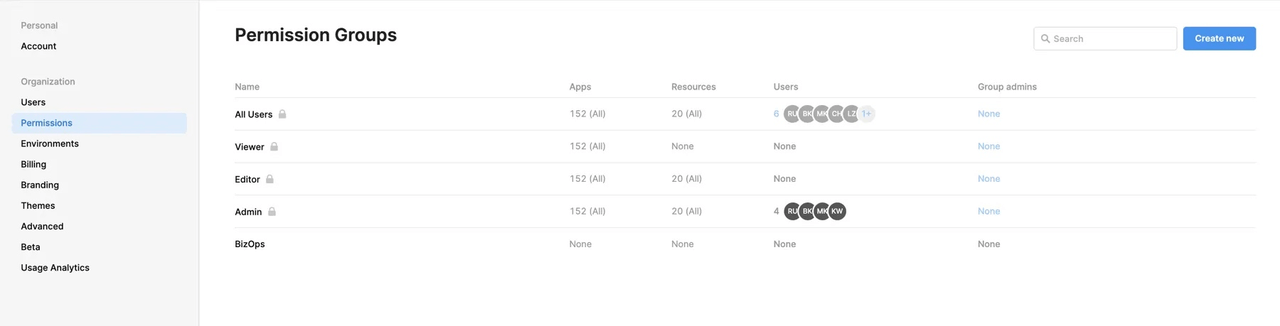
- Permission Granularity: ★★★★ App-, resource-, and query-level control; enterprise users also get row-level security and audit logs.
- Features: Uses Permission Groups to manage roles and resources, with built-in workflows for environment governance and access approvals.
- User Experience: Straightforward admin console, but complex structures require extra governance. Documentation is thorough, ideal for IT-managed setups.
- Extensibility: Supports SSO, SCIM, and SAML integrations and custom APIs for further extensions.
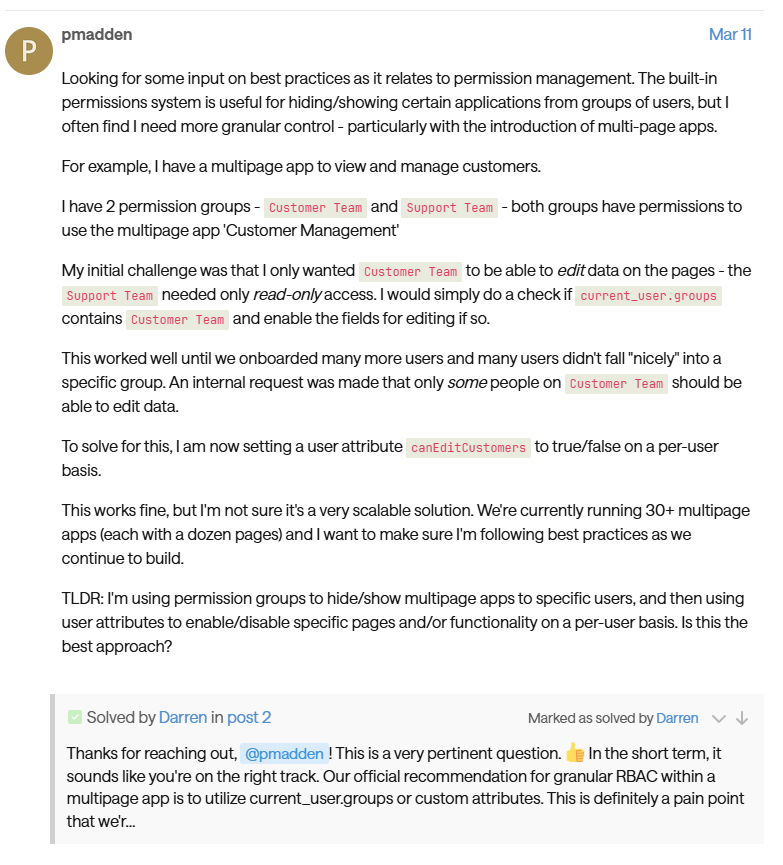
- User Feedback: A user mentioned,that while permission groups work well, fine-grained control (like per-user data editing) still relies on custom attributes — which can be hard to maintain at scale.
 💡 Read more: The Best Open-Source Alternatives to Retool In 2025
💡 Read more: The Best Open-Source Alternatives to Retool In 2025
OutSystems
🔗 Official Site: https://www.outsystems.com
📘 Documentation: https://success.outsystems.com/documentation/11/user_management/user_roles
-
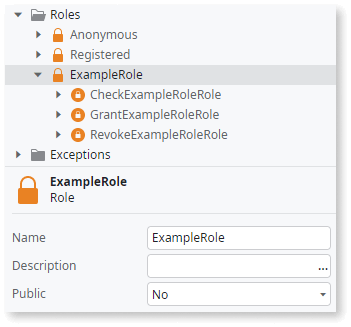
Permission Granularity: ★★★★ Access at screen, module, entity, and UI control levels, with conditional logic in the backend.
-
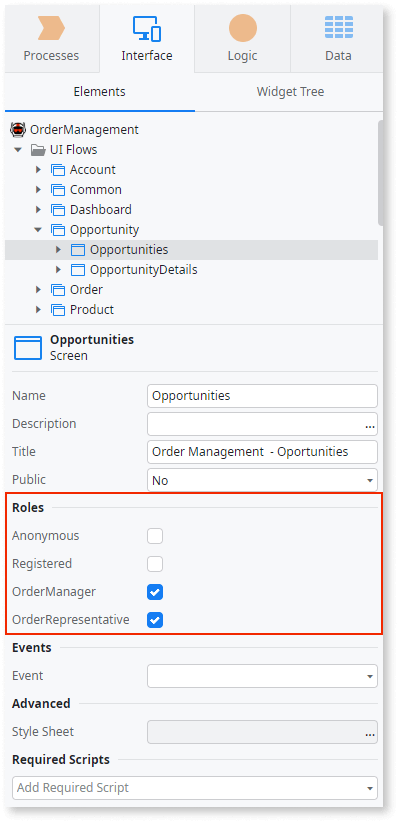
Features: Built-in, end-to-end role management and access control, allowing granular permissions for modules, screens, actions, and data.
-
User Experience: Clear and robust framework, but configuration depends on the IDE (Service Studio), which can feel less intuitive. Maintenance becomes heavier at scale.
-
Extensibility: Supports secure extensions, custom logic, and integration with identity systems such as Azure AD, Okta, and LDAP.
-
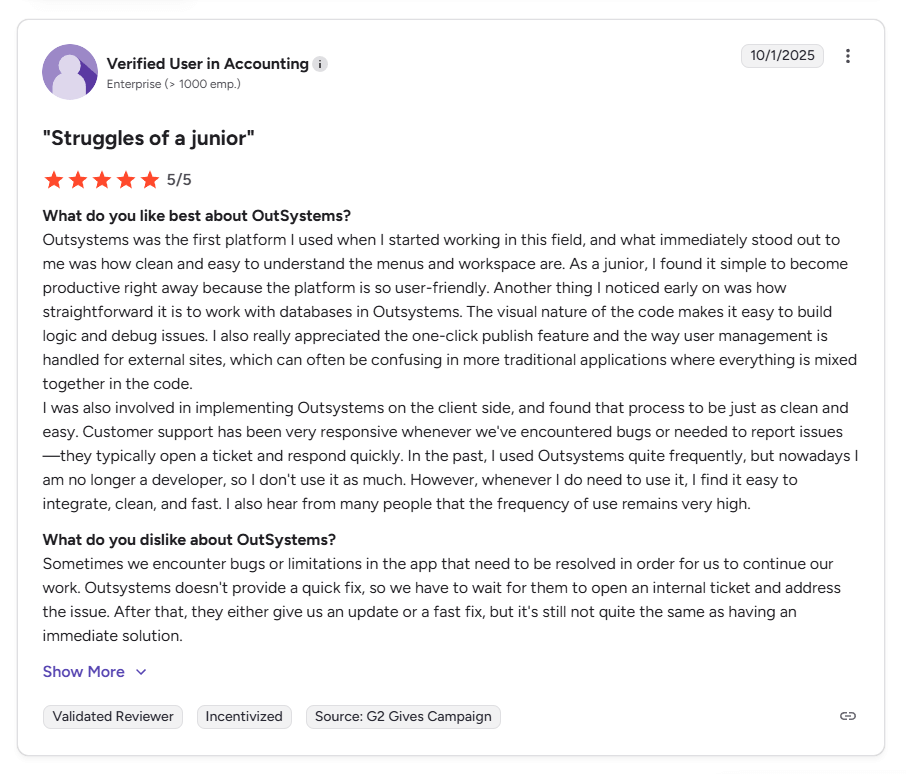
User Feedback: G2 reviewers praised its clean, visual interface for external user and permission management — eliminating the messy “code-mix” common in traditional apps.
Conclusion
Each no-code and low-code platform takes a different approach to RBAC — but all strike a balance between security, flexibility, and usability.
- 🟢 NocoBase: The most advanced open-source RBAC system, with field- and condition-level control and a visual setup. Perfect for teams needing granular control and self-hosting flexibility.
- 👉 Click here to try NocoBase’s RBAC system in action.
- 👉 Read the NocoBase Official RBAC Design Guide for more details.
- 🟡 Appsmith: Balanced and easy to use, great for internal tools, but advanced access features are paywalled.
- 🟡 Budibase: Simple and fast to learn for small teams; limited permission depth and user caps remain its drawbacks.
- 🟠 Mendix / OutSystems: Robust, enterprise-grade systems with strong integration and governance, yet high setup complexity and cost.
- 🟠 Retool: Secure and user-friendly, though per-user control across large apps still needs manual logic.
If this helped you, feel free to share it with others exploring no-code, low-code, or RBAC topics!
Related reading:
- 14 AI-Powered Low-Code Platforms on GitHub Worth Watching
- Top 11 Open Source No-Code AI Tools with the Most GitHub Stars
- Top 18 Open Source AI Agent Projects with the Most GitHub Stars
- Top 20 Open Source AI Projects with the Most GitHub Stars
- Top 8 Open Source MCP Projects with the Most GitHub Stars
- Top 7 Open Source Web Applications with the Most GitHub Stars
- Top 40 Open-source Developer Tools with the Most GitHub Stars