📝 注:この記事は 2026 年 1 月 21 日に最終更新されました。最新の情報を提供するため、定期的に情報を更新しています!😊
Why RBAC Matters
In modern enterprise applications, controlling who can access which data and perform which actions is a foundational yet critical capability. As organizations grow, systems become more complex, user roles diversify, and the demands for data security, access control, and compliance become increasingly strict. At this point, a clear, maintainable, and scalable access control system becomes essential.
One of the most widely used and practical models for this purpose is RBAC—Role-Based Access Control.
💬 Hey, you’re reading the NocoBase blog. NocoBase is the most extensible AI-powered no-code/low-code development platform for building enterprise applications, internal tools, and all kinds of systems. It’s fully self-hosted, plugin-based, and developer-friendly. → Explore NocoBase on GitHub
The core idea behind RBAC is simple: permissions are assigned to roles, and users gain permissions by being assigned roles. In other words, instead of assigning permissions to each user individually, you define a set of roles and their associated permissions, then assign users to the appropriate roles.
This design is especially effective in organizations with multiple roles, layered permissions, and cross-system collaboration.
💡 Read More: How to Build Efficient CRUD Applications?
Core Concepts of RBAC
At its heart, the RBAC model answers a single question:
Who (User) can do what (Permission) to which resource (Resource)?
To address this, RBAC breaks down access control into four key elements:
1. User
An individual who uses the system. This could be an employee, external partner, or system account. A user can be assigned one or more roles.
2. Role
A role represents a job function or responsibility—such as Sales Rep, Sales Manager, or Admin. A role is not a person but an abstract grouping of permissions.
For example:
- A Sales Manager might have permissions to:
- View all customer data
- Update sales statuses
- Assign leads to other sales reps
- A Sales Rep, on the other hand, might only be able to:
- View their own customer records
- Add follow-up notes
3. Permission
A permission defines what action can be taken on a resource. Common actions include:
- Read (view)
- Create
- Edit / Update
- Delete
- Approve, export, print, or other custom actions
4. Resource
The object being accessed or controlled. This could be:
- Customer database
- Contracts
- Financial reports
- Files, records, or UI modules
Permissions are only meaningful when tied to specific resources.
A typical RBAC structure might look like this:
| User | Role | Permissions | Resource |
|---|---|---|---|
| Alice | Sales | View, Create | Customer Records |
| Bob | Manager | View, Edit, Approve | Customer Records |
| Charlie | HR Admin | View, Edit | Employee Profiles |
| David | Finance Team | View, Export | Financial Reports |
This structure decouples user accounts from specific permissions. Instead of managing access per user, you only need to maintain the relationship between roles and permissions. This makes the access control system clear, consistent, and easy to maintain.
Common Design Patterns in RBAC
While the concept of RBAC is straightforward, permission systems often become messy in real-world implementations—and can end up being one of the most difficult parts to maintain.
To avoid confusion and ensure long-term scalability, we recommend following these four steps when designing a clear and extensible RBAC system:
1. Define Roles
Roles are the backbone of any RBAC system. Each role represents a group of users with similar responsibilities and access requirements.
Common ways to define roles:
- By organizational structure (e.g., Sales, Finance, HR)
- By functional responsibilities (e.g., Data Entry, Reviewer, Administrator)
Example roles:
- Sales Representative
- Team Lead
- HR Manager
- Finance Staff
- System Administrator
Recommendation: Keep the number of roles manageable. Avoid “one user, one role” patterns. Each role should represent a general set of permissions for a type of user.
2. Define Resources and Actions
Next, identify the resources in your system that require access control, and the actions that can be performed on them.
Examples of resources:
- Customer Data
- Contract Management
- Approval Workflows
- Financial Reports
Examples of actions:
- View (Read)
- Create
- Edit (Update)
- Delete
- Approve
- Export
These resources and actions form the horizontal axis of your permission model.
3. Map Permissions to Roles
Once roles, resources, and actions are defined, you can map permissions to roles.
Key questions to consider:
- What resources can each role access?
- What actions are allowed on those resources?
- Does your system support multi-role assignment (users with multiple roles)?
- Do you support role inheritance (e.g., Senior Sales inherits from Sales)?
Examples:
- Sales Rep: can view and create their own customers
- Team Lead: can view all customers, assign leads, and approve deals
- Admin: unrestricted access to all resources
At this stage, many teams produce a Role–Resource–Action matrix, which becomes the foundation for configuration and audits.
Example permission matrix:
| Role / Resource | Customer Data | Contract Management | Approval Workflow | Financial Reports |
|---|---|---|---|---|
| Sales Rep | View (own) / Create / Edit (own) | View (own) / Create / Edit (own) | — | — |
| Team Lead | View (all) / Create / Edit / Export | View / Edit | Submit for approval | — |
| HR Manager | — | — | Approver | View / Edit (employee data) |
| Finance Staff | — | View | — | View / Export |
| System Admin | Full Access | Full Access | Full Access | Full Access |
4. Implement Field-Level and Conditional Permissions
Basic RBAC typically controls access at the resource level. However, many real-world systems require more granular control, such as field-level or condition-based permissions.
✅ Field-Level Permissions:
- HR can view all employee records but can only edit salary fields for their own department
- Finance staff can export invoice numbers but cannot view internal comments
✅ Conditional Permissions:
- Sales reps can only view or edit records they created
- In approval workflows, only records with the status “Pending Approval” can be modified
These advanced capabilities are often what separate basic implementations from truly robust RBAC support in any tool or platform.
How to Implement RBAC in Real Projects: A NocoBase Example
Let’s say you’re building a CRM system and need to assign different levels of data access and operational permissions to team members. Below is a typical RBAC implementation process—demonstrated step by step using NocoBase’s CRM system.
1. Who Will Use the System?
Start by managing all users centrally in the Users & Permissions module. In NocoBase, you can organize users into departments—for example, placing all sales reps under the “Sales” department. This lays the foundation for data segmentation and approval routing based on organizational structure.

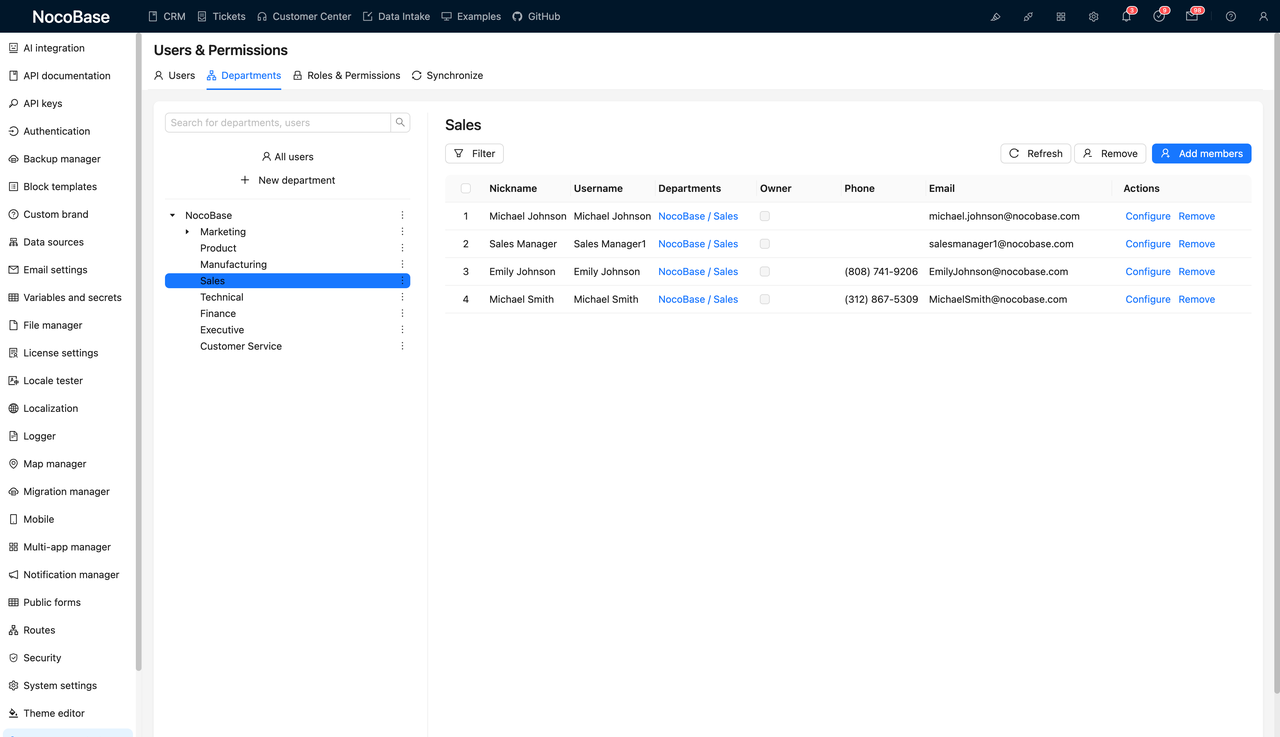
2. What Are Their Roles?
Next, define roles for different user types in the Roles & Permissions section. For instance:
- Sales – regular sales reps who manage their own clients
- Sales Manager – oversees the entire team and has approval privileges
- Admin – full access for system maintenance
Each role can be assigned to one or more users.
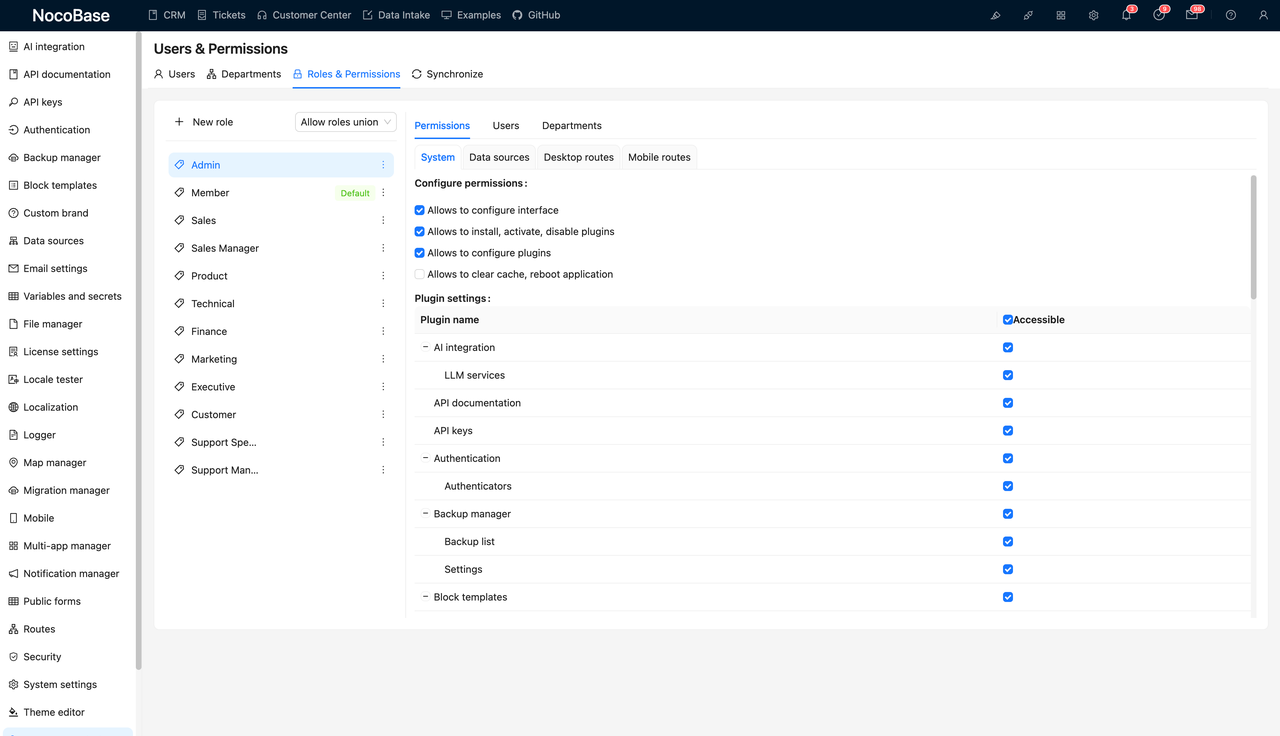
3. What Data Can They Access and Modify?
Configure permissions for each role on key data collections like Customers, Leads, and Opportunities. You can set granular controls such as:
- Can they add, view, edit, delete, import, or export data?
- Can they only access records they created?
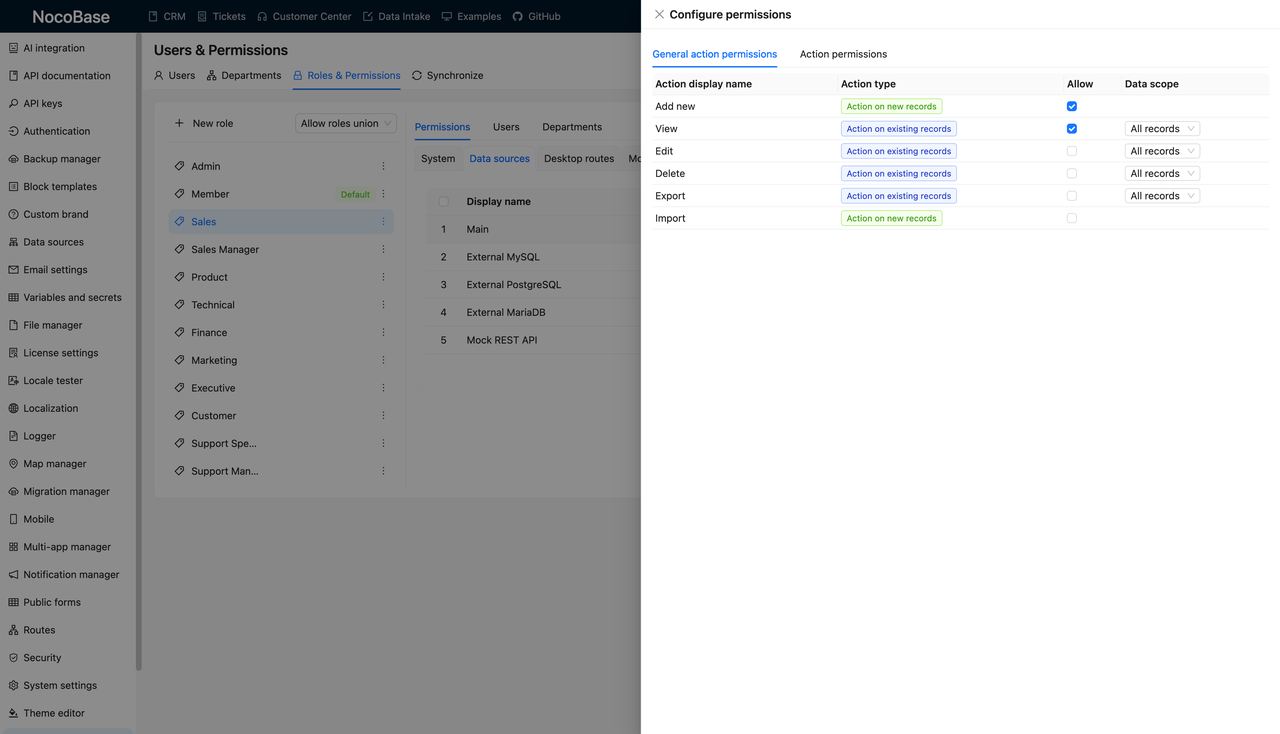
4. What Modules Should They See?
Not everyone needs access to every part of the CRM. In NocoBase, you can control which page modules are visible to each role—both on desktop and mobile.
For example:
- Sales may only see customer management and follow-up records
- Sales Managers may access dashboards and approval centers
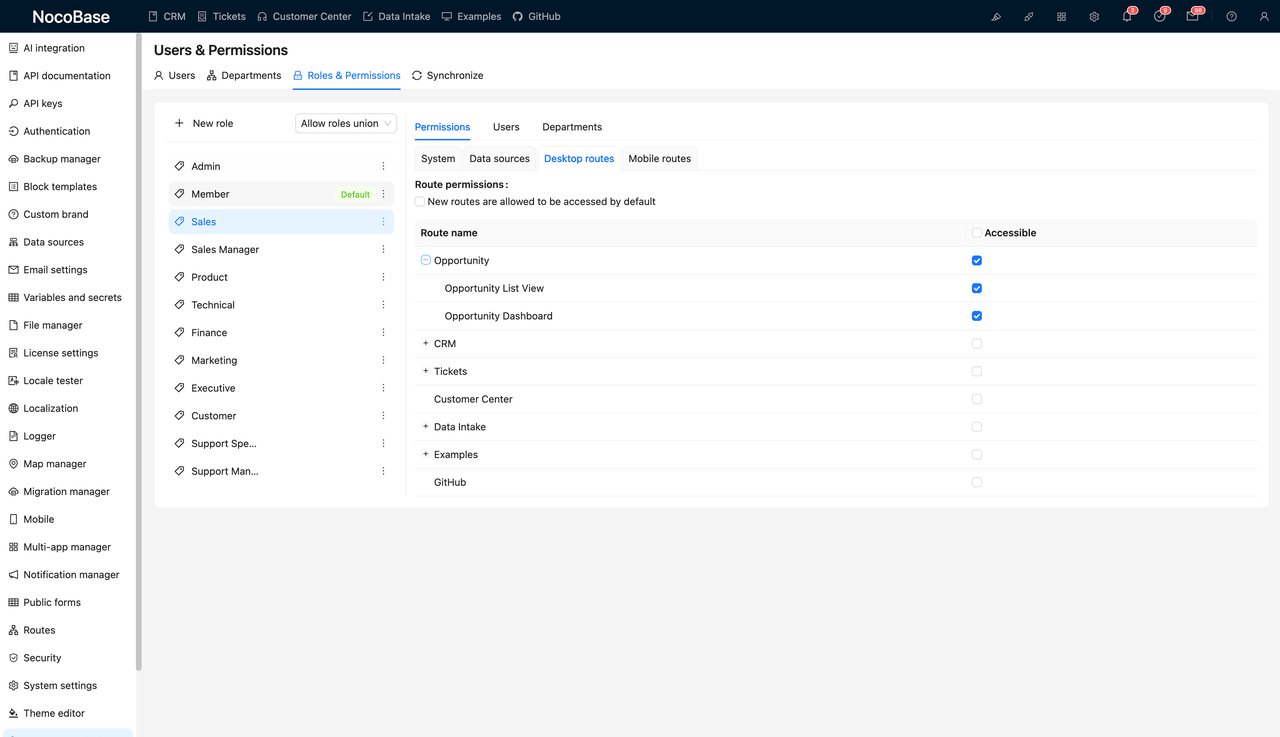
5. How Should Permissions React to Org Structure?
With roles and departments in place, you can define conditional permissions for more dynamic control. For example:
- Users can only view data from their own department
- Managers can only approve leads submitted by their direct reports
- After approval, a record automatically gets reassigned to the manager
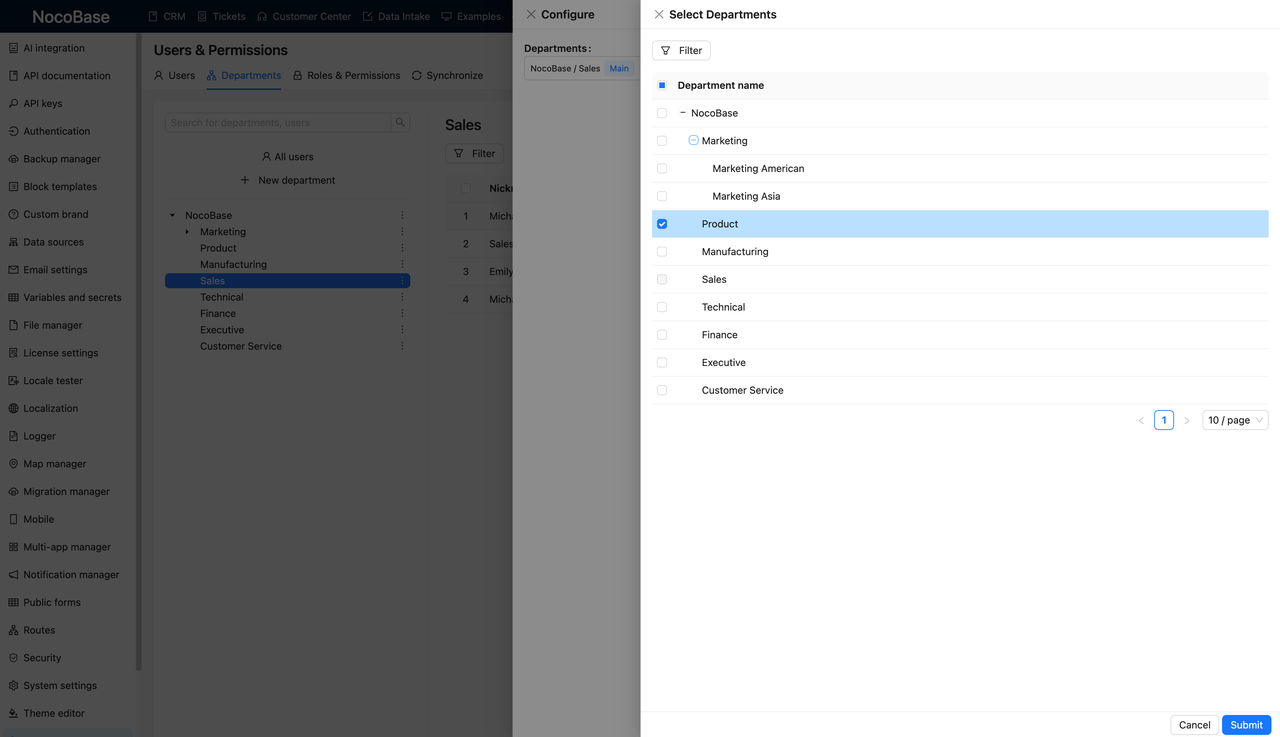
By following these five steps, you can quickly implement a real-world-ready RBAC system in NocoBase. From user identity → page access → data operations → dynamic rules, every step can be visually configured without writing a single line of code. This approach works for both simple use cases and complex business processes.
Summary
In modern business systems, RBAC is a fundamental mechanism for ensuring data security, clear responsibilities, and smooth collaboration.
A well-designed permission system should offer:
- Clear structure – who can access what, and what actions they can take, should be easy to understand
- Flexible configuration – adaptable to organizational changes and evolving business needs
- Maintainability – accessible to non-developers for configuration and management
With the right tools, permissions no longer need to be hardcoded. They can be visually modeled, centrally managed, and continuously improved. This not only strengthens security but also streamlines collaboration and speeds up development.
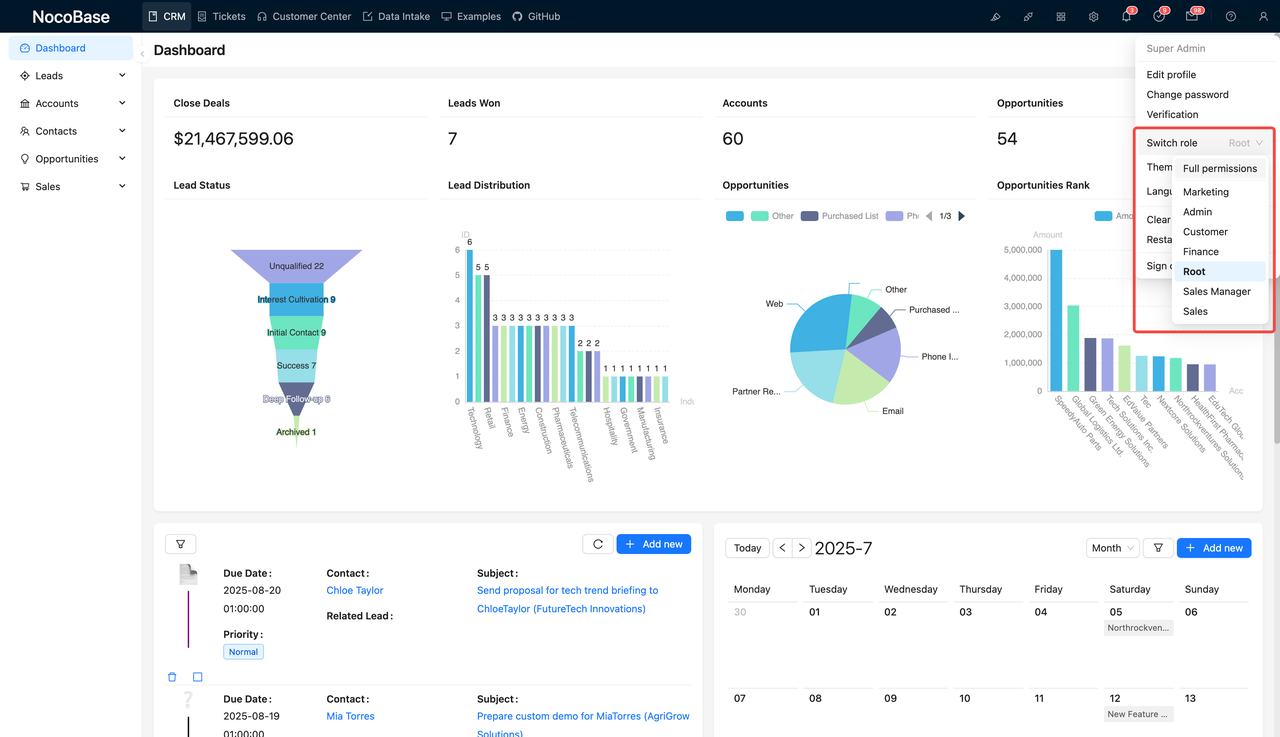
📌 Want to see how RBAC works in practice? We’ve preconfigured a full set of roles, data permissions, page controls, and conditional rules in the NocoBase CRM demo.
👉 Click here to try NocoBase’s RBAC system in action.
Related reading: